MinUWet Administration Guide
Test version: Jan 11, 2005
MinUWet is a tool used in
conjunction with the Network Authentication Applicance
(NAA) servers as part of a coherent plan to improve campus wired and wireless
security.
MinUWet is considered an agent application, which means it
executes on the user’s computer (typically laptops). It detects the level of compliance with
campus security standards (like recent operating system updates and antivirus
definitions) and reports the results to the current NAA server. The NAA then determines whether the client
machine is a significant or acceptable security risk.
Basic Functioning
For this discussion, a working knowledge of the pre-MinUWet
NAA is assumed.
When the NAA finds a new client, it can determine the client operating
system using standard web technologies.
Once the OS is classified (Linux, Mac, Windows, undetermined, etc.),
the client is assigned a profile based on the OS.
The client profile for a PDA could conceivably be different from a Mac
profile. However, initially we will
consider only the following profiles:
-
Windows Untrusted
-
Windows Trusted
-
Other OS - Trusted
If we create MinUWet agents for other
operating systems, we would introduce similar “Trusted” versus “Untrusted” profile distinctions. At present, Windows is the largest source of
problems, so it is the one we will tackle first.
A newly discovered Windows computer is considered “Windows Untrusted”. The user
is free to continue with that designation – in which case the only protocols
allowed after authentication will be HTTP and possibly a few others. HTTP is essential because it is required for
the client computer to get Windows and antivirus updates over the Internet.
If the user agrees to use MinUWet, and MinUWet’s results are positive, the user is upgraded to
“Windows Trusted” status and is given premium network access to many otherwise denied protocols.
MinUWet not only checks for valid
updates, it will proactively force the antivirus client to poll for updates if
none were downloaded in the current day.
The screen during this time is self explanatory:
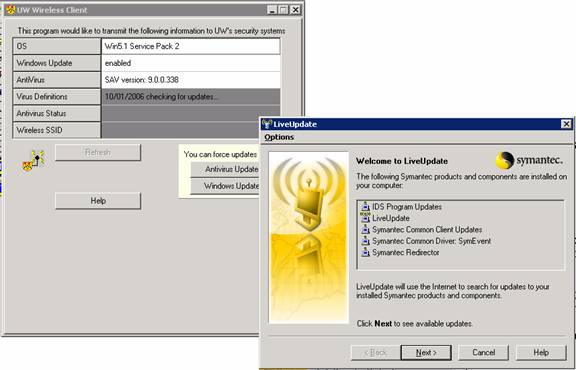
The agent then shares the results with the server along with a cryptographic
hash. The hash ensures someone isn’t
pretending to be MinUWet. In the process, MinUWet
also verifies that the server is who it claims – alerting the user to potential
man-in-the-middle or other attacks aimed at identity theft.
The results of the MinUWet submission are
returned from the server as a web page that MinUWet
displays. It appears similar to:
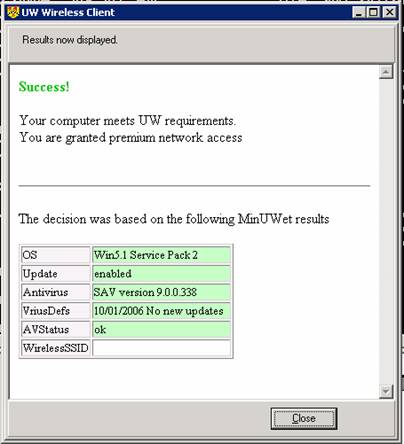
The content is actually produced by the PHP script running on the
NAA. Until production use, the script is
running on a standard Engineering web server.
This content can be changed as needed, just like the NAA login and
post-login pages.
Testing the System
The fully functional prototype is accessible via the web for testing
right now. The only missing pieces are:
-
It does not actually restrict your network traffic, that cannot be done until we move the PHP script to
the NAA. But the logic is all complete.
-
The code does not presently verify that the current web
server is a valid NAA – again that doesn’t make sense until it is actually on
an NAA
-
Only Symantec brands of AntiVirus
have been tested (versions 9 and greater, enterprise and pri
Simply point your browser to:
http://www.eng.uwaterloo.ca/~erick/minuwet/classify.php
See also the minuwetd section below for
additional instructions.
Getting the Agent to the
Client
The agent can be delivered to the client using the Web.
While users should be wary of downloading active content, MinUWet will be digitally signed with the
credentials: nexus.uwaterloo.ca. I am
currently working out the details for signing with Reg
Quinton and Thawte.
Users must already trust active content from Microsoft.com and others,
it’s reasonable to assume they will trust us.
For computers on a domain (eg. ADS or Nexus), we
could pre-install a copy (via GPO), so the user never has to download dynamic
content.
Notes on Prodding Antivirus
Updates
MinUWet’s ability to update the
antivirus definitions is no small feat, because only a power user or
administrator can run Symatec’s utilities. In other words, a well managed laptop with
unprivileged user accounts would seem to be disadvantaged.
The solution is a three step effort based on the administration of the
client computer:
- If the user
is a power user or administrator, we simply spawn the antivirus update
application.
- If the system
a managed computer (eg. ADS, Nexus, etc.) and the user is unprivileged, we look for the presence
of the system service named “minuwetd”, which
can spawn the antivirus updates for the user. Minuwetd
cloaks the update application with system privileges. The strategy is somewhat similar in
principle (though vastly different in implementation) to a setuid solution in Unix. Minuwetd can
be distributed to computers at installation time or using a GPO for domain
based computers.
- Failing the
above automatic solutions,
we simply ask the user for a valid userid/password
capable of running the antivirus update application.
The net result is that #1 and #2 work automatically – and we expect
that they will cover the majority of the cases.
When #3 is used (the last resort), there is always the possibility the
user cannot proceed if he does not know the password. For this reason, the NAA should be tuned to
relax the rules so that the definition of recent could be as liberal as “this
last week”.
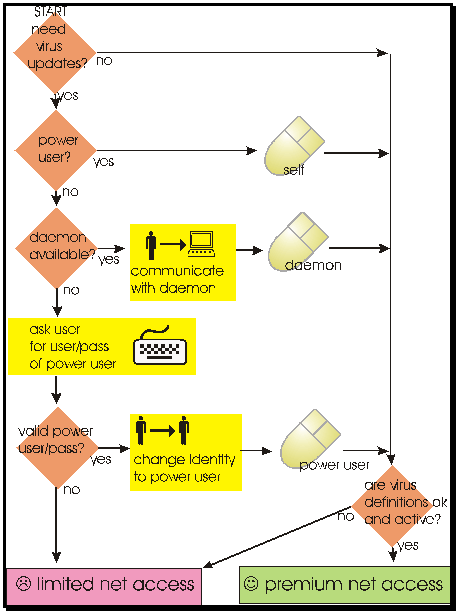
Figure 1 - Updating Antivirus Without
Total Privilegs
Installing MinUWetD
If you want to test the optional daemon/service for unauthenticated, it
can be downloaded from http://www.eng.uwaterloo.ca/~erick/minuwet/mindaemon.exe
and must initially be run with /install to install, and optionally with /silent
to indicate it should not pop up a message box.
The daemon or system process should be configured to always start at bootup. The service
does not consume any CPU cycles until MinUWet
connects to it.
For testing, you can turn it on or off with the Window commands:
net start minuwetd
and net stop minuwetd