Password Stores on Windows
Windows does not store passwords in plaintext, it usually keeps them in to hash formats known as LanManager and Windows password hashes. Windows, including Server 2007 and Vista, keep both hashes on hand.
LanManager is a lower quality mechanism than the Windows hash, and it is kept for backwards compatibility with older LanManager applications including Windows 95 and 98.
The LanManager hash has is most interesting because it is very easy to crack. Whenever Windows is given a password of 14 or fewer characters, it keeps a LanManager hash as well as the Windows hash. For passwords of 15 characters or more, only the Windows hash is stored.
First, consider the more secure Windows password hash system. It is computed as an MD4 hash on the Unicode password string. The result is a irreversible hash of 16 bytes, meaning there is no way to derive the source password from the hash. MD4 is known to have a few weaknesses, particularly that sometimes a different password can be found which resolves to the same hash, known as a collision. It is considered a reasonably secure password hash mechanism, where brute force is usually necessary to crack the password or find a collision. However, there also exists tables of pre-converted hashes which one can build or buy, which can instantly convert a hash to its plaintext version. The best defense is a long and somewhat random password.
The LanManager hash is a hacker’s dream. The password made case insensitive (it is converted to all upper case), and then broken into two 7 character strings, and uses DES to compute two eight byte hashes which are then concatenated to form a 16 byte password hash. Passwords shorter than 14 characters are null padded.
Since the two halves are treated as separate, this means hackers need only compute hashes for up to seven characters, and they can be compared to both the first and second seven character sequences. Also, the case insensitivity means hackers need not bother computing hashes for the 26 characters ‘a’ through ‘z’. This greatly reduces the time to do a crypto attack.
For modern systems such as Windows XP, the LanManager hash can be cracked quickly, then the hacker need only try all the permutations of capitalization to crack the case sensitive seven character password, which is a much smaller attack space than if only Windows (MD4) password hashes were stored.
To gauge the security of a real system, I collected the hashes of 78,000 real users and started computing passwords by performing dictionary attacks and then brute force for the remainder.
My password cracking machine was an old 1.5 GHz Pentium 4 computer with 512MB of RAM and an IDE disk running FreeBSD 6.2 and John the Ripper.
Of the 78,154 passwords, 9,807 were greater than 14 characters and were thus stored with only the Windows format hash code. This left 68,347 with LanManager hash codes and the following graph shows how quickly those were cracked on the relatively slow computer.
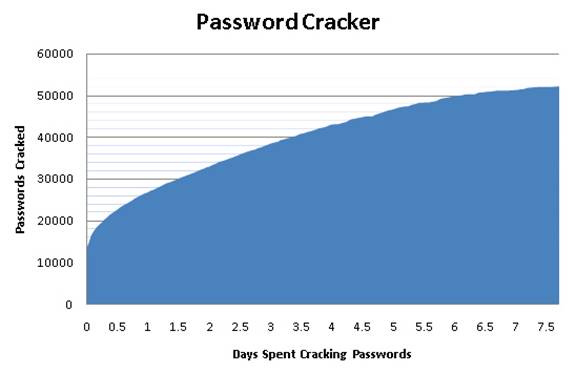
About LM hash 14,700 passwords were cracked in the first hour, but the rate quickly slowed as passwords got more complicated. Around 10,000 passwords were not cracked at the end of the week long attack, and toward the end of this attack the passwords were each taking much longer to crack. But it is a fairly accurate statement that anything stored as an LM hash is not terribly secure. While one can use the LM hashes to audit password security, it’s hard to set a cutoff because almost all passwords can be cracked with a little time.
It is possible to turn off the storage of LM hashes with a domain controller switch. We have tested this on the nexustest domain. The configuration switch doesn’t discard existing LM hashes, it just stops storing new ones when passwords are changed. So setting this switch doesn’t offer an immediate improvement in security, but the benefits will be eventually realized.
One consequence of discarding the LM hashes is that it is no longer possible to use LM hashes for password auditing. However, we are willing to forgo that capability and set the switch on the Nexus domain at the end of the Fall 2007 school term.
Update: we found NTLM hashes were used by so many web sites that it would break too many things if we disabled them.